Best Cyber Security Course in Navi Mumbai
6 Month Programs
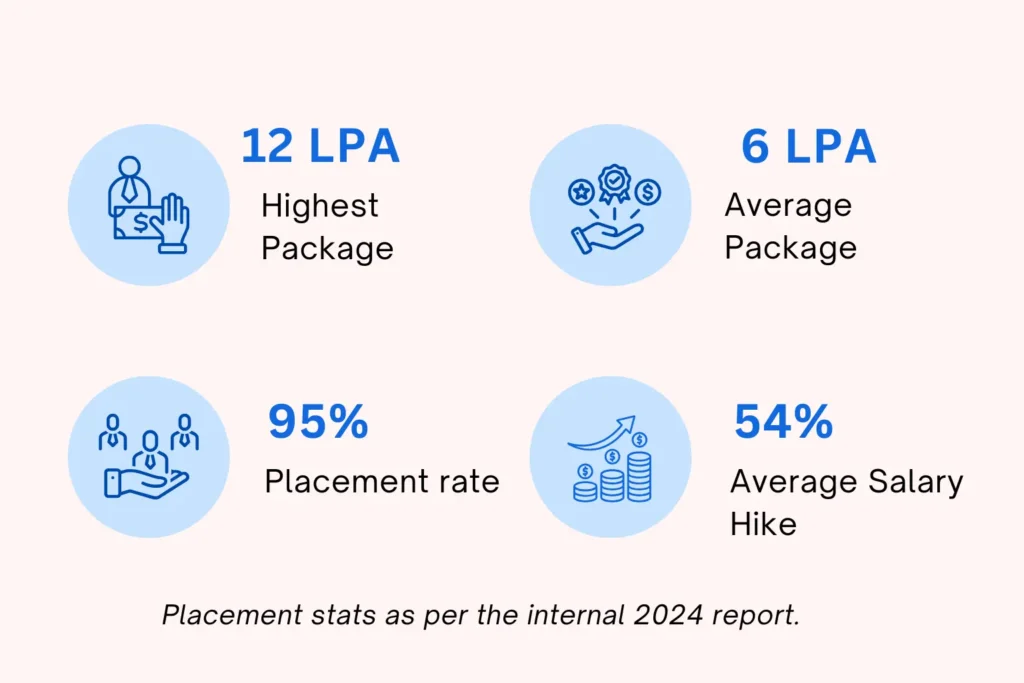
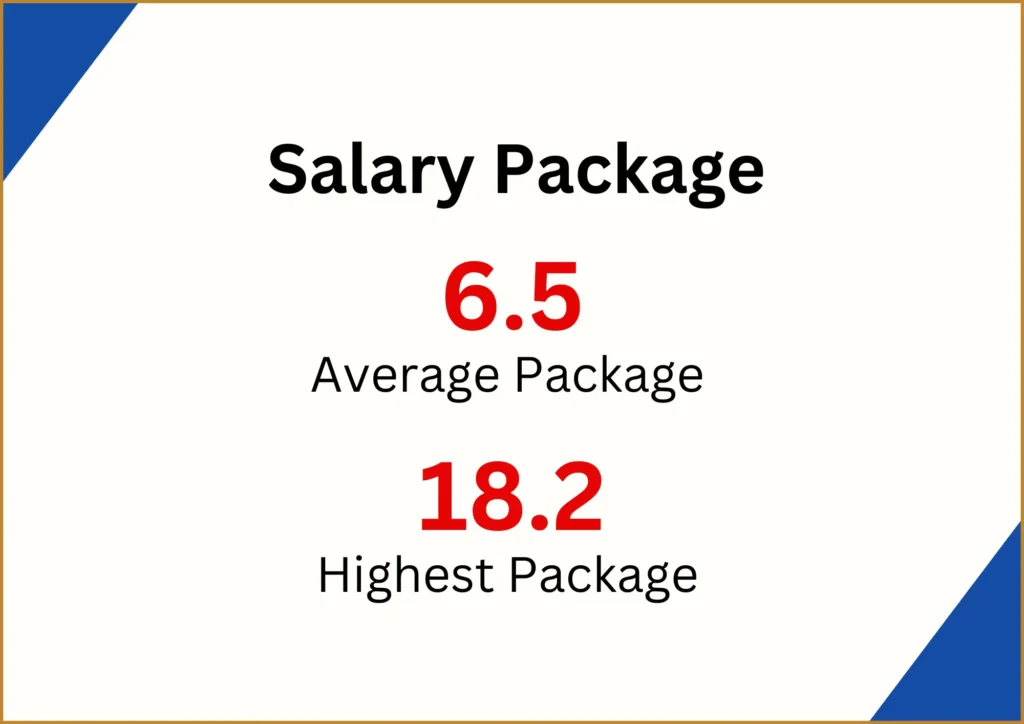
100% Placement Assistances
Global Certification
Complete Placement Assistance for Students

Student's Placement Felicitation
Student's Placement Felicitation
At MindForge Infotech, we believe in celebrating success and honoring hard work. Our Placement Felicitation Ceremony is a proud tradition where we recognize the achievements of our students who have successfully secured positions in top companies.
Recently Placed Students

Karan Patel
Profile: Graduate Engineering Trainee
(Company: SBI General Insurance)

Mahek Ansari
Profile: Assistant System Engineer
(Company: TCS )

Ajjay Bhagyakr
Profile: Digital Marketing Executive
(Company: Apex Fresh)

Subro Mandal
Profile: Digital Marketing Executive
(Company: Nisarg Yatri)
Online & Offline Cyber Security Course Syllabus
- PROFESSIONAL CERTIFICATION
- PG CERTIFICATION

CCNA
Cisco Certified Network Associate
CCNA: Network Fundamentals, Network Access, IP Connectivity, IP Services, Security Fundamentals, Automation & Programmability, Routing and Switching Essentials, WAN Technologies, Routing Protocols, Network Address Translation (NAT), Quality of Service (QoS)

Ethical Hacking
Find Security Vulnerabilities
Ethical Hacking: CCNA, CEHV12, Footprinting and Reconnaissance, Scanning Networks, Vulnerability Analysis, System Hacking, Malware Threats, Sniffing and Packet Analysis, Social Engineering, Denial-of-Service (DoS) Attacks, Session Hijacking, Web Application Hacking, Wireless Network Hacking, Cryptography and Encryption, Evading IDS, Firewalls, and Honeypots, Cloud Security, Ethical Hacking Tools Overview, Reporting and Documentation, Final Project: Full Penetration Testing Simulation

Penetration Testing (VAPT/LPT)
Security Exercise
Penetration Testing (VAPT/LPT): Introduction, Scanning & Enumeration, Exploitation concepts, Burpsuite, WebApp Common Vulns, Network VAPT, Owasp Top 10, Privlege Escalation, Automated Scanning, CTF’s, Bug Hunting

Mobile Hacking
Protecting Mobile Devices
Mobile Hacking: Introduction, Android Architecture and Security Model, Interacting With Android Devices, Android Hacking and Exploitation, Android Pentesting

Cloud Security Testing
Protect Cloud-Based Data
Cloud Security Testing: CCNA, Basic to advance kali linux, CEHv12, Network pentesting, Web-application pentesting, Active directory pentesting, API Pentesting, Mobile Pentesting, Cloud Security, Cyber Law

Cyber Law
legal Framework
Cyber Law: Fundamentals of Cyber Law, E-commerce- Legal issues, Intellectual Property Issues and Cyberspace – The Indian Perspective, Cyber crime and Digital Evidence – the Indian Perspective

CCNA
Cisco Certified Network Associate
CCNA: Network Fundamentals, Network Access, IP Connectivity, IP Services, Security Fundamentals, Automation & Programmability, Routing and Switching Essentials, WAN Technologies, Routing Protocols, Network Address Translation (NAT), Quality of Service (QoS)

Ethical Hacking
Find Security Vulnerabilities
Ethical Hacking: CCNA, CEHV12, CCNA, CEHV12, Footprinting and Reconnaissance, Scanning Networks, Vulnerability Analysis, System Hacking, Malware Threats, Sniffing and Packet Analysis, Social Engineering, Denial-of-Service (DoS) Attacks, Session Hijacking, Web Application Hacking, Wireless Network Hacking, Cryptography and Encryption, Evading IDS, Firewalls, and Honeypots, Cloud Security, Ethical Hacking Tools Overview, Reporting and Documentation, Final Project: Full Penetration Testing Simulation

Mobile Hacking
Protecting Mobile Devices
Mobile Security: Introduction, Android Architecture and Security Model, Interacting With Android Devices, Android Hacking and Exploitation, Android Pentesting

Penetration Testing (VAPT/LPT)
Security Exercise
Penetration Testing (VAPT/LPT): Introduction, Scanning & Enumeration, Exploitation concepts, Burpsuite, WebApp Common Vulns, Network VAPT, Owasp Top 10, Privlege Escalation, Automated Scanning, CTF’s, Bug Hunting

Cloud Security
Protect Cloud-Based Data
Cloud Security: CCNA, Basic to advance kali linux, CEHv12, Network pentesting, Web-application pentesting, Active directory pentesting, API Pentesting, Mobile Pentesting, Cloud Security, Cyber Law

Cyber Law
legal Framework
Cyber Law: Fundamentals of Cyber Law, E-commerce- Legal issues, Intellectual Property Issues and Cyberspace – The Indian Perspective, Cyber crime and Digital Evidence – the Indian Perspective

Kali Linux
Debian-based Linux distribution
Kali Linux: Introduction to Kali Linux, Command Line Basics, Networking Concepts, Information Gathering, Vulnerability Assessment, Exploitation Tools, Wireless Network Attacks, Password Attacks, Web Application Testing, Social Engineering, Privilege Escalation, Maintaining Access, Reporting and Documentation, Final Project: Real-World Penetration Test Simulation
AWS/Azure
Amazon Web Services
AWS/Azure: Introduction to Cloud Computing & AWS, AWS Compute Services, AWS Storage Services, Networking & Content Delivery, AWS Database Services, Identity and Access Management (IAM), Security and Compliance, Monitoring and Optimization, High Availability and Disaster Recovery, DevOps and Automation on AWS, Final Project: Build and Deploy a Scalable Cloud Architecture
Cyber Security Training Reviews





Job Oriented Cyber Security Certifications


Cyber Security Tools You'll Learn
Working with a variety of cyber security (ethical hacking) tools on a daily basis is a need of becoming an ethical hacker. These are some of the tools you will learn how to use in the online cybersecurity course offered by MindForge Infotech.

Career Opportunities After Cyber Security Training


Why Choose MindForge Infotech
Industry-Expert Instructors
Learn from seasoned professionals with real-world experience in the IT industry.
Flexible Learning Options
Choose between online and in-person classes to suit your schedule and learning preferences.
Hands-On Training
Gain practical skills through hands-on projects and real-world case studies.
Certification Preparation
Prepare for industry-recognized certifications that enhance your employability and career prospects.
Job Placement Assistance
Benefit from dedicated career services, including job placement support and internship opportunities.
Lifetime Access to Materials
Enjoy lifetime access to course materials, ensuring you can revisit and refresh your knowledge anytime.
MindForge Infotech Events
Women's Day Celebration 2025
At MindForge Infotech, we proudly celebrated Women’s Day to honor the strength, resilience, and achievements of women. The day was filled with inspiring activities, heartfelt appreciation, and empowering moments that highlighted the incredible contributions of women in shaping a brighter future.
Holi Celebration
This year, MindForge Infotech, came alive with the vibrant hues of Holi! From splashes of color to endless laughter, our Holi celebration was a perfect mix of joy, unity, and festive spirit.
A Ghibli Glow: Celebrating Moments at MindForge Infotech
Holi Celibration
This year, MindForge Infotech, came alive with the vibrant hues of Holi! From splashes of color to endless laughter, our Holi celebration was a perfect mix of joy, unity, and festive spirit.
A Ghibli Glow: Celebrating Moments at MindForge Infotech
Frequently Asked Questions
We offer a variety of IT training courses, including web development, data science, cybersecurity, cloud computing, and more.
You can enroll in a course by visiting our website, selecting your desired course, and following the registration process. For assistance, you can contact our admissions team.
Prerequisites vary by course. Some courses require basic computer knowledge, while others may require specific programming skills. Check the course details for specific requirements.
Yes, we provide a certificate of completion for all our courses. Additionally, some courses prepare you for industry-recognized certifications.
Yes, we offer both online and in-person classes to accommodate different learning preferences.
Cyber Security course fees vary depending on the program. You can find detailed pricing information on our website under each course description.
Yes, we have a dedicated career services team that provides job placement assistance, resume building workshops, and interview preparation.
Digital Marketing Course durations depend on which type of course you choose professional or master. Check the course details for specific timelines.
Yes, we offer flexible payment plans and EMI options for eligible students. Please contact our financial aid office for more details.


